Fishing for hackers: Analysis of Linux Server Attack
By A Mystery Man Writer

The rise of Linux malware: 9 tips for securing the OSS

The Weak Link: Recent Supply Chain Attacks Examined

What is SQL Injection, SQL Injection Attack
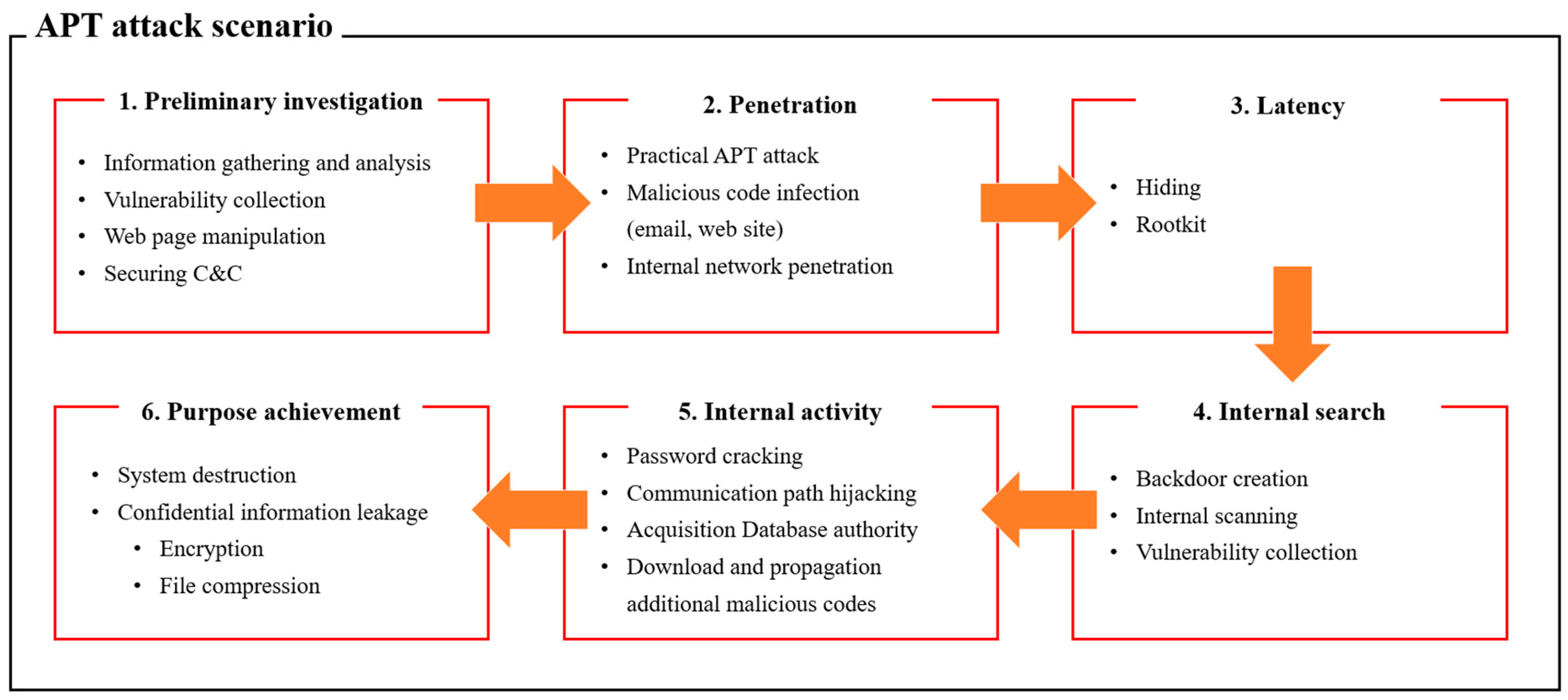
Applied Sciences, Free Full-Text

10 top anti-phishing tools and services

Query Graph of Scenario: Linux-2 (on the left) and its Detected

10 industry-defining security incidents from the last decade
Kali Linux Penetration Testing Tutorial: How to Use Kali Linux

Analysis of Attacks That Install Scanners on Linux SSH Servers